The developer of RegCleaner, jv16 PowerTools, Uninstalr, WinFindr, Startup Timer, ScreenshotX, System Examiner and Windows Update Fixer.
It is never easy to keep your information secure online.
Often, you might have conversations where there’s confidential information flow between you and another party. When was the last time you took into consideration the probability that there’s leakage of information during this communication?
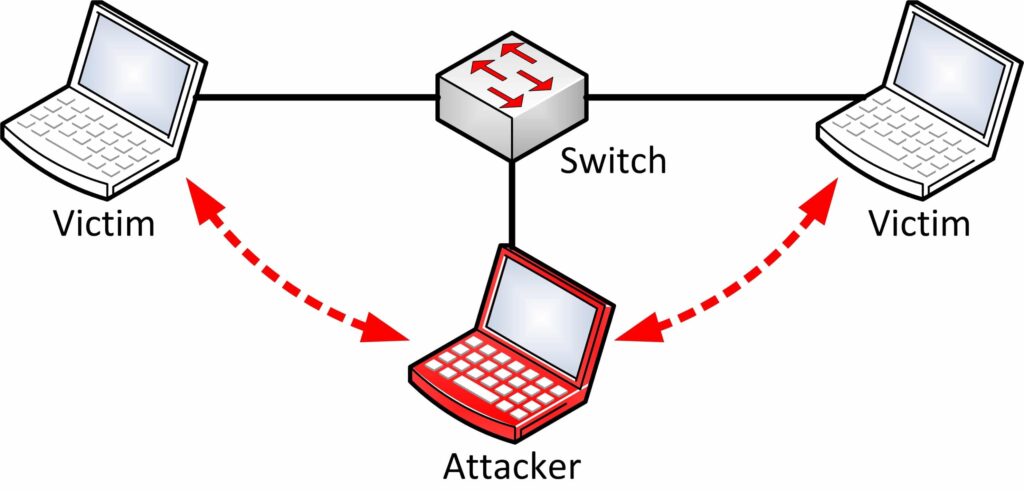
In internet security terminology, MITM is a form of active eavesdropping. The attacker becomes an intermediary between all communications happening between victim systems and the gateway.

He makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection. When in fact, the entire conversation is controlled by the attacker.
The attacker can easily sniff and modify information at will. This type of attack attack happens in both wired and wireless networks.
In this post, we will teach you how MITM attacks work and how to keep safe from them.
What are MITM Attacks?
A man in the middle attack is one of the most common and dangerous kinds of attacks. You may not even realize that your traffic is being intercepted since the attack is more or less passive.
Moreover, this type of attack is quite frequent. Freely available hacking tools can allow attackers to automatically set up these attacks.
MITM attacks over the Intranet can appear in companies where an employee intercepts the traffic resulting in leakage of confidential information.
In an external network, if you use an unencrypted wireless access point (Wi-Fi) for accessing confidential information, then there is a possibility of this information being intercepted by an attacker.
He can exploit the router, using malicious programs. What he will do is configure their laptop as a Wi-Fi hotspot, selecting a name commonly used in public areas like coffee shops and airports.
The attacker simulates a secure online environment in order to persuade two parties to form a mutual authentication. He must be able to intercept all relevant messages passing between the two victims and inject new ones.
How MITM Attacks Work?
A man in the middle attack requires three players:
- The targeted user.
- An entity – the legitimate financial institution, database, or website.
- The cyber criminal who will try to intercept the communication between the two parties.
Critical to the scenario is that the victim isn’t aware of the man in the middle.
A typical communication flow occurs between a client and a server. MITM attacks change up this flow of information drastically. Let’s say you received an email that appeared like a genuine message from your bank, asking you to log in to your account to confirm your contact information.

You click on a link in the email and are taken to what appears to be your bank’s website. This attack also involves phishing, getting you to click on the email appearing to come from your bank. Thinking that you are on a legitimate financial site, you will submit your log-in credentials.
Without knowing, you are handing your sensitive information to the ‘man in the middle’.
The Workflow Of MITM Attacks
Man in the middle attacks take place in two phases:
- Interception
- Decryption
1. Interception
In the first phase, the user traffic is redirected through the hacker’s network before it reaches the sender or receiver’s system. Neither the sender or receiver is aware that their traffic is being rerouted through an attacker’s network.
They may use one or more of the below mentioned tactics to intercept:
-
IP Spoofing
Every computer on the internet has an internet protocol (IP) address. The attacker masks himself as an application and changes headers of IP address.
By spoofing an IP address, an attacker can trick you into thinking you’re interacting with a website or someone you’re not. So, users attempting to access URL of an application will be redirected to the attacker’s website.
Therefore, you will be giving the attacker access to information you’d otherwise not share.
-
ARP Spoofing
In ARP spoofing, the attacker sends fake ARP (Address Resolution Protocol) messages to the user’s system through the IP of another user in the same local network.
-
DNS Spoofing
In DNS Spoofing, the attacker accesses the server and alters the website address record to match his website records thus redirecting the user through the attacker’s website.
It’s a technique that forces a user to a fake website rather than the real one the user intends to visit. You may think you’re visiting a safe, trusted website when you’re actually interacting with a fraudster.
The attacker’s goal is to divert traffic from the real site or capture user login credentials.
-
Email hijacking
Attackers sometimes target email accounts of banks and other financial institutions.
Once they gain access, they can monitor transactions between the institution and its customers. After that, they can spoof the bank’s email address and send their own instructions to customers.
This fools the customers to follow the attacker’s instructions rather than the bank’s.
- Wi-Fi eavesdropping
Attackers set up Wi-Fi connections with very legitimate sounding names. Maybe using similar names to a business nearby.
Once a user connects to the attacker’s Wi-Fi, he will be able to monitor the user’s online activity and intercept important information, such as login credentials, payment card information.
-
Stealing browser cookies
A browser cookie is a small piece of information a website stores on your computer.
An online retailer might store the personal information you enter, such as shopping cart items you’ve selected, on a cookie. So, you don’t have to re-enter that information when you return.
What an attacker can do is hijack your browser cookies. Since cookies store information from your browsing session, attackers can gain access to your passwords, address, and other sensitive information.
2. Decryption
After the data is intercepted, it needs to be decrypted by creating a two-way SSL traffic. There are many methods an attacker can use to achieve this:
-
HTTPS Spoofing

Seeing “HTTPS” in the URL, rather than “HTTP” is a sign that the website is secure and can be trusted (“S” stands for “secure”).
The attacker can send a phony SSL certificate containing the digital thumbprint of the user obtained from a compromised application. After that, the browser verifies it and approves, thus granting access to the attacker.
Basically, the attacker fools your browser into believing it’s visiting a trusted website when it’s not. By redirecting your browser to an unsecure website, the attacker can monitor your interactions with that website and possibly steal personal information you’re sharing.
-
SSL Hijacking
In SSL hijacking, the attacker uses another computer and secure server in order to intercept all the information passing between the server and the user’s computer.
-
SSL Stripping
A connection to a secure server means standard security protocols are in place. SSL stands for Secure Sockets Layer, a protocol that establishes encrypted links between your browser and the web server.
In SSL stripping, the attacker downgrades the application or website off it’s SSL encryption.
How to prevent Man In The Middle Attacks
1. HTTPS in the URL bar
Always check if there is an “HTTPS” in the address of the websites you visit. Avoid visiting or exchanging information across any websites that do not have the security of HTTPS.
2. Avoid connecting to public Wi-Fi routers directly
Never connect to public Wi-Fi routers directly. If there is no option but to use them, ensure you are using a Virtual Private Network or a SSL plugin to safeguard your data privacy.

A VPN encrypts your internet connection on public hotspots to protect the private data you send and receive while using public Wi-Fi.
3. Be cautious of phishing emails
Avoid clicking links in your emails. Instead of clicking on the link provided in the email, manually type the website address into your browser.
Be cautious when it comes to potential phishing emails from attackers asking you to update your password or any other login credentials.
4. Keep your system protected at all times
MITM attacks primarily use malware for execution. Malware and spyware get installed in a computer when your system is not adequately protected using an antivirus program.
You should install a comprehensive internet security solution and always keep the security software up to date. It will identify malicious items you’d never suspect existed, keeping your online activities secure and safe.
Moreover, conduct regular scans to ensure that no malware is transmitting data to attackers.
5. Set up an intrusion detection system (IDS)
The IDS will basically monitor your network. If someone tries to hijack traffic flow, it gives immediate alerts.

It uses the advanced address resolution protocol (like XARP or ARPOn) and implements dynamic host configuration protocol (DHCP). Snooping on switches can limit or prevent ARP spoofing.
Unfortunately, IDS may raise false attack alerts, leading users to disable it.
6. Use the virtual private network (VPN)
Another solution for preventing man in the middle attacks is to use the virtual private network (VPN). It creates additional secure layers when you access the Internet through public Wi-Fi.
Conclusion
Detecting a man in the middle attack can be very difficult.
Since there are very few methods to detect these attacks, prevention is better than cure.
On a higher scale, man in the middle attacks are prevalent in companies which do not use secure email. So, there’s no encryption or other protective measures that prevent attackers from accessing that information.
Typically, you should not use public networks for working on any confidential matters. It’s best to use the public network only for basic purposes like surfing news.